In computer networking, TACACS+ (Terminal Access Controller Access-Control System Plus) is a protocol which provides access control for routers, network access servers and other networked computing devices via one or more centralized servers. TACACS+ provides separate authentication, authorization and accounting services.
Contents |
History
TACACS+ is based on TACACS, but, in spite of its name, it is an entirely new protocol which is incompatible with any previous version of TACACS. TACACS+ and RADIUS have generally replaced the earlier protocols in more recently built or updated networks, although TACACS and XTACACS are still running on many older systems.
Authentication, Authorization and Accounting (AAA)
Whereas RADIUS combines authentication and authorization in a user profile, TACACS+ separates the two operations. Another difference is that TACACS+ uses the Transmission Control Protocol (TCP) while RADIUS uses the User Datagram Protocol (UDP). Most administrators recommend using TACACS+ because TCP is seen as a more reliable protocol.
The extensions to the TACACS+ protocol provide for more types of authentication requests and more types of response codes than were in the original specification.
Protocol details
TACACS+ utilizes TCP port 49. It consists of three separate protocols, which can, if desired, be implemented on separate servers.[1]
TACACS+ offers multiprotocol support, such as IP and AppleTalk. Normal operation fully encrypts the body of the packet for more secure communications. It is a Cisco proprietary enhancement to the original TACACS protocol.
TACACS+ uses APPLE and NETBIOS for operation.
See also
References
External links
- Cisco's TACACS+ RFC draft
- http://www.shrubbery.net/tac_plus/
- http://www.gazi.edu.tr/tacacs Database supported tacacs+
- http://rubyforge.org/projects/tacacs-plus/ A pure Ruby implementation of TACACS+
Single-User Network Access Security TACACS+
- TACACS+ Software 10.3(3) Product Announcement
- PR: "TACACS+ -- New Version of Cisco's Server-Based Security Protocol"
Overview
A major paradigm shift in remote network access is the shift from terminal access to LAN access. Single users are connecting to the corporate network with computers (notebooks or PCs from home) that can sustain complete network connections. These users no longer connect as unfriendly terminals but connect in the same way they do at work: as a LAN user.Companies are moving to the remote node, remote LAN, and remote access server paradigm because it increases user productivity. Remote node technology gives users access to the same corporate network from home or while traveling as they do at work. Connecting to the network means connecting to a NetWare file server or AppleShare. Users are not required to become experts on terminal services and login prompts.
Since the network is now readily available through remote node technology, network access security has become increasingly important. Host security was adequate for terminal access, but network access security is needed for remotely connected users or remote nodes.
General Network Access Security Requirements
Network Access Security (NAS) is evolving from user needs. Network managers are now concerned with three sets of requirements for their NASs: authentication, authorization, and accounting services.
Authentication
Authentication is who is allowed to gain access to the LAN. Simple authorization methods use a database of username and passwords on the terminal server or access server. More advanced authorization systems use methods such as TACACS (a centralized Token card systems) and Kerberos.However, once users are authenticated to use the LAN, they may still need to apply a username password for access to specific services such as UNIX hosts, NetWare, or AppleShare. A good NAS server supports a variety of authentication options.
Authorization
Authorization, the ability to limit network services to different users, is a dynamically applied access list (sometimes called a user profile) based on the username/password pair. This feature is useful for two primary reasons: it helps to limit the exposure of the internal network to outside callers and simplifies the view of the network for the less technical remote access user.Authorization allows users to be mobile. Mobile and temporary users (portable users with modems in hotels and telecommuters with modems or ISDN connections at home) want to connect to the closest local connection and still have the same access privileges of their local networks.
The network administrator must be able to limit network access to users for all access protocols and services (Telnet, IP, IPX, and AppleTalk) while users dial in through the same modem pool. Per-user access list authorization is not limited to specific interfaces but is dynamically assigned to the specific port to which a user attaches. For example, when user A connects to port 1, she can see subnets 1, 2, 3 and AppleTalk zones bldg D, bldg E, and bldg F. When user B connects to port 1, his profile limits him to subnet 1 and AppleTalk zone bldg D.
Since a NAS supports many more remote users than its physical lines, each user or group of users can dial into the same phone rotary and receive access to the network. The access list is based on username and, as such, each NAS, and can support thousands of users in its username and password database.
Accounting
Accounting is the third major requirement in a security system. Network administrators may want to bill departments or customers for connection time. Accounting also provides the ability to track suspicious connection attempts into the network.
General Cisco Network Access Security Features
Following are the general network access security features that are currently available on Cisco Access Servers. These features can be internally stored on an access server or centralized database using TACACS.-----------------------------------------------------------------------------
FEATURE FUNCTION
=============================================================================
Username and password Basic NAS security
Per-user access Basic authentication
lists for IP
Callback Reverses phone charges, extra security for
telecommuters
PAP and CHAP Translates PAP or CHAP to TACACS
Logging Sends start and stop times to external logging server
Absolute time out Limits the time a user can be connected to connect
session limit
Inactivity time out Cisco supports session timeout, which disconnects a
user after a specified time of inactivity. After a
session timeout, another person cannot use the
connection.
Autocommand A user can automatically execute a command
(if it is available in the internal database).
System script Automatically connects a user to a specific host or
other script capabilities
Autoselect Automatically provides users with the service they
need to connect to the access server. Autoselect
supports Telnet, TN3270, SLIP, PPP (for IP or IPX)
and ARA. Autoselect limits the user's access to
services by automatically providing the appropriate
service. For example, a Macintosh user can be
automatically dropped into ARA without an exec
terminal session. This is both a security and ease-
of-use feature.
-----------------------------------------------------------------------------
Manual Service Selection: EXEC
EXEC allows users to connect to the access server "shell," then select services.Users connected to EXEC may specify various services: UUCP, PPP, SLIP, ARA, TN3270, Telnet, or EXEC to manage the router itself.
Connecting to EXEC allows users to manage the access server or router if they have the appropriate privileges.
Internal or Centrally Managed NAS
All of the security features mentioned can be set up and administered internally on a Cisco access server or passed from a Cisco access server to a centralized database. To send the information to a central database and forward the response to the proper Cisco access server requires a specific protocol.Cisco implemented the Terminal Access Controller Access System (TACACS) protocol for this exact reason. It was developed by BBN to support multiple communication servers' username/password authentication. It forwards the user's username and password information to a centralized database that also has the TACACS protocol. The centralized database looks up the information and sends back an accept or deny message, which either allows or denies the user access. The centralized database can be modified to control the authorization from either a simple or complex environment.
Centralized Database and TACACS
A client/server (protocol and server) architecture places all security information on a single, central database, instead of being disbursed around a network in different devices. This is especially useful if there are thousands of users who are using thousands of access servers distributed around the network.A security protocol and server are much more extendible and scalable for large enterprises. TACACS and other remote access security protocols are designed to support thousands of remote connections. In a large network, the user database is usually large, and is best kept on a centralized server. This saves memory in all the access devices and eliminates the need to update every access server when new users are added, or passwords are modified or changed.
TACACS
TACACS is a an industry standard protocol specification, RFC 1492, that forwards username and password information to a centralized server. The centralized server can either be a TACACS database or a database like the UNIX password file with TACACS protocol support. For example, the UNIX server with TACACS passes requests to the UNIX database and sends the accept or reject message back to the access server.
XTACACS
XTACACS defines the extensions that Cisco added to the TACACS protocol to support new and advanced features.XTACACS supports:
- Multiple TACACS servers
- syslog -- Sends accounting information to a UNIX host
- connect -- Where the user is authenticated into the access server "shell" and can Telnet or initiate slip or PPP or ARA after initial
XTACACS is multiprotocol and can authorize connections with:
- SLIP
- enable
- PPP (IP or IPX)
- ARA
- EXEC
- Telnet
TACACS+
TACACS+ allows a separate access server (the TACACS+ server) to provide the services of authentication, authorization, and accounting independently. Each service can be tied into its own database or can use the other services available on that server or on the network. 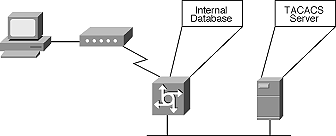
Figure 1: Control Access to Network Via Dial Up
TACACS+ will be supported by the Cisco family of routers and access servers as part of a maintenance of Cisco IOS Release 10.3. This protocol is a completely new version of the TACACS protocol referenced by RFC 1492. Cisco is presenting TACACS+ to the IETF working groups and will contribute to and adopt the emerging NAS protocol standard.
The overall design goal of TACACS+ is to define a standardmethod for managing dissimilar Network Access Servers (NASs) from a single set of management services such as a database. A NAS provides connections to a single user, to a network, or subnetwork, and interconnected networks.
TACACS+ has three major components: the protocol support within the access servers and routers, the protocol specification, and the centralized security database. Similar to an internal security database, TACACS+ supports the following three required features of a good security system.
Authentication
The TACACS+ protocol forwards many types of username password information. This information is encrypted over the network with MD5, an encryption algorithm. TACACS+ can forward the password types for ARA, SLIP, PAP, CHAP, and standard Telnet. This allows clients to use the same username password for different protocols. TACACS+ is extensible to support new password types like KCHAP.
TACACS+ authentication supports multiple challenge and response demands from the TACACS+ server. This allows token card vendors to provide advanced features like sending back a second token-generated number after the first one was manipulated by a security server.
Authorization
TACACS+ provides a mechanism to tell an access server which access list that a user connected to port 1 uses. The TACACS+ server and location of the username/password information identify the access list through which the user is filtered. The access list(s) reside on the access server. The TACACS server responds to a username with an accept and an Access List number which causes that list to be applied.
Accounting
TACACS+ provides accounting information to a database through TCP to insure a more secure and complete accounting log.
The accounting portion of the TACACS+ protocol contains the network address of the user, the username, the service attempted, protocol used, time and date, and the packet-filter module originating the log. For Telnet connections, it also contains source and destination port, action carried (communication accepted, rejected), log, and alert type. Formats are open and configurable.
The billing information includes connect time, user ID, location connected from, start time, and stop time. It identifies the protocol that the user is using and may contain commands being run if the users are connected through exec and Telnet.
Future TACACS+ accounting enhancements will provide connect time updates, which will send an update for current connect time to the accounting server every x minutes. This feature allows companies like Internet providers to bill a customer for an open session even if the access server restarts and loses the initial start time. Service providers can significantly minimize lost billing time.
The auditing information provides which commands + arguments, location connect from.
The protocol provides enough information so that a server can produce intruder detection routines, reporting statistics, number of packets, and number of bytes.
Users want servers to prevent multiple uses of the same username/password so that customers with flat rates do not share their account with others. Although the decision to give access is made on the server, the protocol is flexible enough to provide the necessary information to detect multiple passwords.
Third-Party Security Solutions
TACACS is an open protocol and can be ported to any username or password database. Many users now want token card support for their remote dial-in access users. Many token card client server companies have ported the TACACS protocol to their central databases. This allows remote node users to connect to a network through a Cisco access server, while using a third-party database and token cards for the remote users. 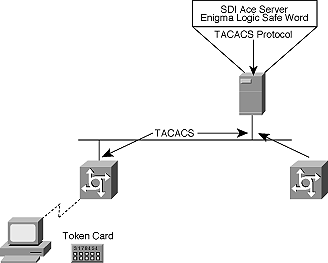
Figure 2: TACACS and Token Card Support
Companies that support this solution today include:
- Enigma Logic
- Security Dynamics
- Digital Pathways
Advantages of the TACACS+ Protocol:
- TCP-based for more security
- Provide three separate protocol components, each of which can be implemented on separate servers
Authentication provides complete server control of the authentication process, which includes:
- login and password query
- Challenge/response
- Messaging support (any)
- Encrypted in MD5
- Replaceable with Kerberos 5
Authorization allows "remote" access control and enhanced granularity. Features include:
- One authentication
- Authorization for each service
- Per-user access list and user profile
- Users can belong to groups
- IP and Telnet support (IPX, ARA future)
- Any access or command and permission or restrictions
- Initial connection upon starting any command or service
- Primary service
- Exec or autoselected protocol
- Secondary service
- Commands from exec or control protocol like PPP NCP and based on connection location
Examples of the "AAA" Functionality
The authorization component in TACACS+ allows greater levels of control over user actions and can be used to create separate administrative groups that are based on user functionality. For example, a network manager might want to restrict a user to perform certain functions on the access server or router. Within the access server, a user might be restricted to PPP or SLIP and only be permitted to connect to a specific host address. Another example of the flexibility of the authorization subsystem is forcing a user to connect to a particular host if an attempt is made to connect to a specific host. In the case of the router's command line user interface, a restriction might be placed on executing particular EXEC commands such as reload.The authentication protocol can also generate an autocommand. Once a user is authenticated, this runs any command within the access server system and is very powerful for complete access management. Network managers can use the accounting component to track user activity for a security audit trail or to provide billing information. A report might be structured to provide: user identity, start and stop times, executed commands, number of packets, and number of bytes.
Password aging is another example of the capabilities that are now available with TACACS+. A server supporting TACACS+ can send a message back to users, telling them to change their passwords as part of the login sequence. They will not be allowed access unless they change their passwords at that time.
-----------------------------------------------------------------------------
TACACS
FEATURE INTERNAL XTACACS TACACS+
=============================================================================
AUTHENTICATION
PAP/CHAP * * *
System script * * *
Autocommand * * *
DialBack 95 * 95
Username/password * * *
Use MD5 encryption *
Token card support * *
Via Kerberos 5 95
For exec * * *
For PPP (IP and IPX) * * *
For ARA * * *
Multiple challenge and response *
Router access authentication * * *
Support for rcmd *
Try multiple authentication types * *
-----------------------------------------------------------------------------
AUTHORIZATION * *
Per user-IP (SLIP and PPP) * * *
Per user IPX 95 95 95
Per user ARA 95 95 95
exec prompt access * *
exec and PPP IP address * *
exec and Telnet * * *
Router commands * * *
User-changeable Dependent on Yes, but only
password server with one server
-----------------------------------------------------------------------------
ACCOUNTING
Time connection start * *
Time connection finish * *
Total connection time * *
# packets, # bytes
Which commands + argument 95
Location connect from 95
User ID * *
User protocol * *
Use UDP *
Use TCP *
Absolute time out
Inactivity time out
-----------------------------------------------------------------------------
The TACACS+ Protocol Spec
TACACS+ also provides a general-purpose protocol specification that allows the TACACS+ protocol to be integrated into standard databases. The TACACS+ protocol specification will make integration of the TACACS+ protocol into third-party or customer authentication/security databases easier and it also provides more functionality. Current third party support for TACACS includes Security Dymanics, Enigma Logic, and more new customers to be announced.Third-party token support will be enhanced with TACACS+ in that the custom database will be able to handle challenge response mechanisms for tokencards and other advanced authentication systems.
General
TACACS+ sample server C code and protocol specification will be available from Cisco Connection Online (CCO) on the World Wide Web (http://www.cisco.com) and character-based bulletin board (telnet cco.cisco.com), and through anonymous FTP (ftp.cisco.com).Cisco is working with the IETF to standardize these security protocols. And is working with other centralized security protocols like Radius. Cisco will participate in the evolution of a single standards-based NAS protocol.
Posted: Mar 30 11:46:18 1995



1 comment:
Thanks for the article.In your article you covered almost all the necessary information. You also mentioned some network access security features, some examples, some pictures very effectively.
digital signature PDF
Post a Comment